- Enable Tls 1.2 On Chrome For Macsportfasr Hp
- Enable Tls 1.2 On Chrome For Macsportfasr Mac
- Enable Tls 1.2 On Chrome For Macsportfasr Laptop
Applies to: Configuration Manager (Current Branch)
When enabling TLS 1.2 for your Configuration Manager environment, start by ensuring the clients are capable and properly configured to use TLS 1.2 before enabling TLS 1.2 and disabling the older protocols on the site servers and remote site systems. There are three tasks for enabling TLS 1.2 on clients:
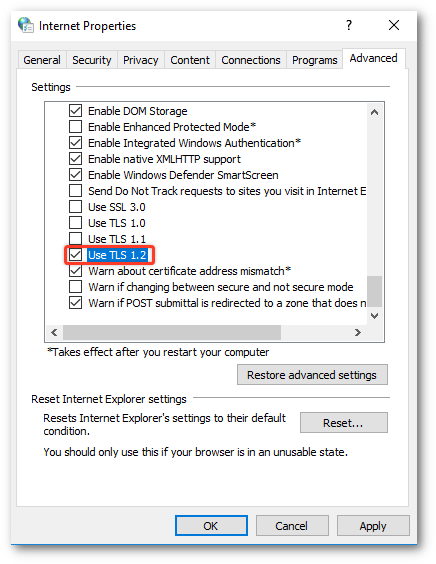
To enable TLS 1.1 and/or TLS 1.2 protocols on web browsers, see the list below. Microsoft Internet Explorer, Google Chrome, Mozilla Firefox, Opera, Apple Safari.
- Update Windows and WinHTTP
- Ensure that TLS 1.2 is enabled as a protocol for SChannel at the operating system level
- Update and configure the .NET Framework to support TLS 1.2
For more information about dependencies for specific Configuration Manager features and scenarios, see About enabling TLS 1.2.
Further down there is a link to activate TLS 1.2 The information is dated and when you follow through it says Chrome uses by default. There was a link to report problems, I did, Said info was wrong and outdated. When you look at the specific browser they want it doesn't acknowledge Windows 10 is out and knows not of Windows 10. Enable TLS 1.1 and 1.2 on Windows 7 at the SChannel component level. Per the TLS-SSL Settings article, for TLS 1.1 and 1.2 to be enabled and negotiated on Windows 7, you MUST create the 'DisabledByDefault' entry in the appropriate subkey (Client) and set it to '0'. These subkeys will not be created in the registry since these protocols are. Dec 13, 2019 Before you enable TLS 1.2 on any server components, update Windows to support TLS 1.2 for client-server communications by using WinHTTP. If you enable TLS 1.2 on server components first, you can orphan earlier versions of clients. To access the ASC Employee Portal, ensure your browser(s) have TLS 1.1 and/or TLS 1.2 enabled. Below are instructions for changing the relevant settings in the most common internet browsers. Please use the Google Chrome instructions on a VCH workstation. Open Google Chrome. Click Alt F and select Settings.
Update Windows and WinHTTP
Windows 8.1, Windows Server 2012 R2, Windows 10, Windows Server 2016, and later versions of Windows natively support TLS 1.2 for client-server communications over WinHTTP.
Earlier versions of Windows, such as Windows 7 or Windows Server 2012, don't enable TLS 1.1 or TLS 1.2 by default for secure communications using WinHTTP. For these earlier versions of Windows, install Update 3140245 to enable the registry value below, which can be set to add TLS 1.1 and TLS 1.2 to the default secure protocols list for WinHTTP. With the patch installed, create the following registry values:
Important
Enable these settings on all clients running earlier versions of Windows before enabling TLS 1.2 and disabling the older protocols on the Configuration Manager servers. Otherwise, you can inadvertently orphan them.
Verify the value of the DefaultSecureProtocols registry setting, for example:
If you change this value, restart the computer.
The example above shows the value of 0xAA0 for the WinHTTP DefaultSecureProtocols setting. KB 3140245: Update to enable TLS 1.1 and TLS 1.2 as default secure protocols in WinHTTP in Windows lists the hexadecimal value for each protocol. By default in Windows, this value is 0x0A0 to enable SSL 3.0 and TLS 1.0 for WinHTTP. The above example keeps these defaults, and also enables TLS 1.1 and TLS 1.2 for WinHTTP. This configuration ensures that the change doesn't break any other application that might still rely on SSL 3.0 or TLS 1.0. You can use the value of 0xA00 to only enable TLS 1.1 and TLS 1.2. Configuration Manager supports the most secure protocol that Windows negotiates between both devices.
If you want to completely disable SSL 3.0 and TLS 1.0, use the SChannel disabled protocols setting in Windows. For more information, see How to restrict the use of certain cryptographic algorithms and protocols in Schannel.dll.
Ensure that TLS 1.2 is enabled as a protocol for SChannel at the operating system level
TLS 1.2 is enabled by default. Therefore, no change to these keys is needed to enable it. You can make changes under Protocols to disable TLS 1.0 and TLS 1.1 after you've followed the rest of the guidance in these articles and you've verified that the environment works when only TLS 1.2 enabled.
Verify the SecurityProvidersSCHANNELProtocols registry subkey setting, as shown in Transport layer security (TLS) best practices with the .NET Framework.
Update and configure the .NET Framework to support TLS 1.2
Determine .NET version
Enable Tls 1.2 On Chrome For Macsportfasr Hp
First, determine the installed .NET versions. For more information, see How to determine which versions and service pack levels of the Microsoft .NET Framework are installed.
Install .NET updates
Install the .NET updates so you can enable strong cryptography. Some versions of .NET Framework might require updates to enable strong cryptography. Use these guidelines:
NET Framework 4.6.2 and later supports TLS 1.1 and TLS 1.2. Confirm the registry settings, but no additional changes are required.
Update NET Framework 4.6 and earlier versions to support TLS 1.1 and TLS 1.2. For more information, see .NET Framework versions and dependencies.
If you're using .NET Framework 4.5.1 or 4.5.2 on Windows 8.1 or Windows Server 2012, the relevant updates and details are also available from the Download Center.
Enable Tls 1.2 On Chrome For Macsportfasr Mac
Configure for strong cryptography
Configure .NET Framework to support strong cryptography. Set the SchUseStrongCrypto registry setting to DWORD:00000001. This value disables the RC4 stream cipher and requires a restart. For more information about this setting, see Microsoft Security Advisory 296038. Stupid testwatermelon gaming.
Make sure to set the following registry keys on any computer that communicates across the network with a TLS 1.2-enabled system. For example, Configuration Manager clients, remote site system roles not installed on the site server, and the site server itself.
For 32-bit applications that are running on 32-bit OSs and for 64-bit applications that are running on 64-bit OSs, update the following subkey values:
For 32-bit applications that are running on 64-bit OSs, update the following subkey values:
Note

The SchUseStrongCrypto setting allows .NET to use TLS 1.1 and TLS 1.2. The SystemDefaultTlsVersions setting allows .NET to use the OS configuration. For more information, see TLS best practices with the .NET Framework.
Next steps
In one of the strangest stories of the year, the COVID-19 virus has halted plans by major browsers to drop support for the ageing and insecure Transport Layer Security (TLS) 1.0 and 1.1 protocols.
Mozilla Firefox and Google’s Chrome developers sneaked out the move in recent days with only Microsoft Edge team bothering to formally announce the sudden reprieve on Tuesday.
In fairness, with COVID-19 throwing development schedules into minor chaos browser development teams probably have other things on their minds right now anyway.
While a temporary delay, it’s still an unexpected retreat for an industry which had showed unity in collectively deciding to banish TLS 1.0 and the lesser used TLS 1.1 by early 2020.
TLS, of course, is the protocol used to encrypt network communication, most prominently the HTTPS used by web browsers to connect securely to websites.
While TLS 1.2 and the recent 1.3 are now widely supported, versions 1.0 and 1.1 are now so old they’ve accumulated numerous weaknesses that render them insecure.
Attacks have included BEAST in 2011, Lucky Thirteen in 2013, and the POODLE SSL downgrade attack from 2014, and several others. Things got so bad the PCI DSS compliance standards were updated to insist that servers taking credit card payments stop supporting it in 2018 at the risk of big fines.
But what’s this got to do with COVID-19?
That’s less well explained, with Microsoft referring only to “current global circumstances”. Mozilla was more forthcoming:
We reverted the change for an undetermined amount of time to better enable access to critical government sites sharing COVID19 information.
That’s a polite way of saying that, prior to COVID-19, those sites would have been allowed to wither as users trying to visit them were confronted with warnings about the sites’ support for insecure protocols.
In other words, the seriousness of COVID-19, and the possibility that at least some people might try to visit these sites, has now overridden these concerns.
Ironically, this is the very issue that’s dogged the phasing out of support for TLS 1.0 – the annoying fact that some websites that should know better haven’t been turning off support, hence the need for browser makers to step in to do it from the client end.
The question is how long this logic can hold.
Officially, the three browser makers mentioned in this article have all said they plan to revert to plan A and drop support for TLS 1.0 and 1.1 by the late spring or summer. But what happens if COVID-19 is still a problem?
Assuming these sites offering COVID-19 advice haven’t banished TLS 1.0 and 1.1 by the cut offs, that could either force more delays or a decision to press ahead regardless.
Daewoo g25s forklift manuals freeeagleaustin. The larger truth is abandoning anything in software has become difficult. When the moment comes, there are bound to be losers and holdouts.
It’s been the bane of operating systems, such as Windows and Android, for years. Now this phenomenon is repeating itself on a smaller scale in the normally obscure world of the protocols used to quietly secure traffic between browsers and websites.
Latest Naked Security podcast
LISTEN NOW 201314 chris neil game worn helmetottawa senators game used.
Enable Tls 1.2 On Chrome For Macsportfasr Laptop
Click-and-drag on the soundwaves below to skip to any point in the podcast. You can also listen directly on Soundcloud.
